From Logs to Proof: Making VPC Flow Logs Work for You
Everyone collects VPC Flow Logs—but few know how to unlock their real power. In this blog, we’ll show how to transform raw logs into a validated detection pack, mapped to MITRE ATT&CK. From Recon to Exfiltration, discover how logs become proof of defense, not just storage.
Teamregulateaiml
9/2/20252 min read
From Logs to Proof: Making VPC Flow Logs Work for You
Most cloud teams collect VPC Flow Logs. Few can prove they’re catching real attacker behavior with them. That’s the problem—logs pile up, but when asked, “Do these detections actually work?” the answer is often silence.
This blog is about changing that. By mapping VPC Flow Logs to MITRE ATT&CK and wrapping them in a validated detection pack, you move from raw telemetry to evidence-backed security findings.
Why Flow Logs Still Matter
Flow logs capture network metadata—who talked to whom, on which ports, and how much data moved. They don’t give packet payloads, but when normalized (via Cribl) and pushed into a SIEM (Splunk, Sentinel), they help uncover:
Reconnaissance – external port scans, probing for misconfigured services.
Lateral Movement – east-west traffic between workloads that shouldn’t talk.
Exfiltration – unusual outbound transfers, often to foreign destinations.
The trick is to stop treating them as a compliance checkbox and start treating them as provable security controls.
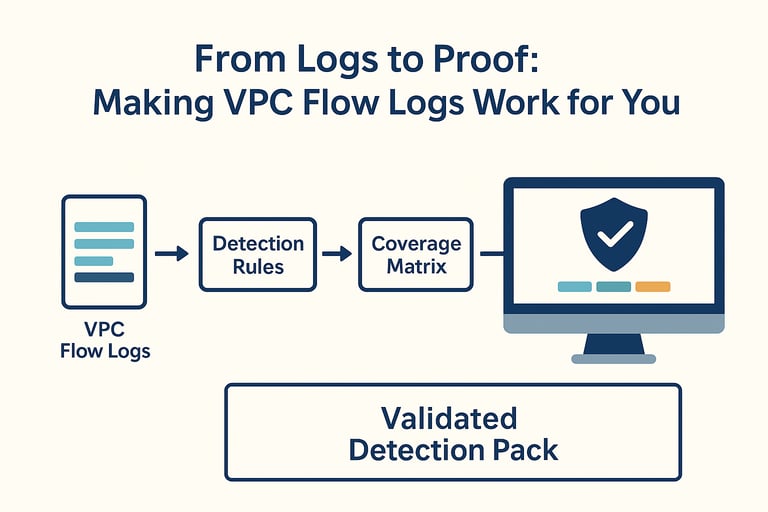
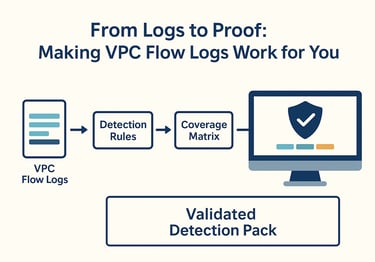
Building the Detection Pack
Instead of scattered alerts, this approach creates a pack of rules, mappings, and validation tests.
1. Detection Rules in KQL & SPL
Reconnaissance (ATT&CK T1046 – Network Scanning)
kql
VPCFlow
| where Direction == "Inbound" and Action == "ACCEPT"
| summarize Count = count() by SrcIP, DstPort
| where Count > 100 and DstPort in (22, 3389, 1433)
spl
index=vpc_flow_logs action=ACCEPT
| stats count by src_ip, dest_port
| where count > 100 AND dest_port IN (22, 3389, 1433)
Exfiltration (ATT&CK T1041 – Exfiltration over C2 Channel
VPCFlow
| where Direction == "Outbound" and BytesSent > 50000000
| extend Geo = geo_info(DstIP)
| where Geo not in ("IN", "US")
2. Coverage Matrix (Log Source → ATT&CK Technique)
This isn’t theory—it’s evidence that flow logs can map directly to attacker behaviors.
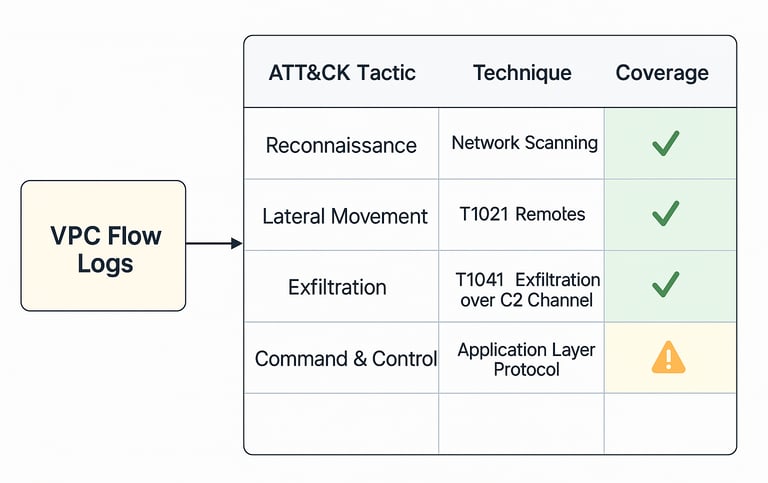
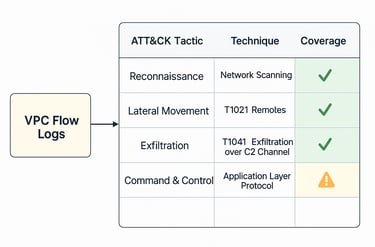
3. Why This Matters for Security Leaders
CISOs and SOC leads don’t just want rules. They want proof:
Mapped to MITRE ATT&CK → aligns with frameworks leadership trusts.
Multi-SIEM ready → useful in Splunk, Sentinel, or others.
Clear coverage → shows what’s in place, what’s planned.
📌 Key Takeaway (Part 1): Flow logs don’t have to sit idle. With structured detection engineering, they become provable defenses against recon, lateral movement, and exfiltration.
In Part 2, we’ll dive into testing, unit validation, and MTTD/MTTR metrics—so you don’t just build detections, you can prove they work.